c08c98415395b76371581432be55381f0f6e2b40,w3af/plugins/audit/format_string.py,format_string,_analyze_result,#format_string#,58
Before Change
//
// I will only report the vulnerability once.
//
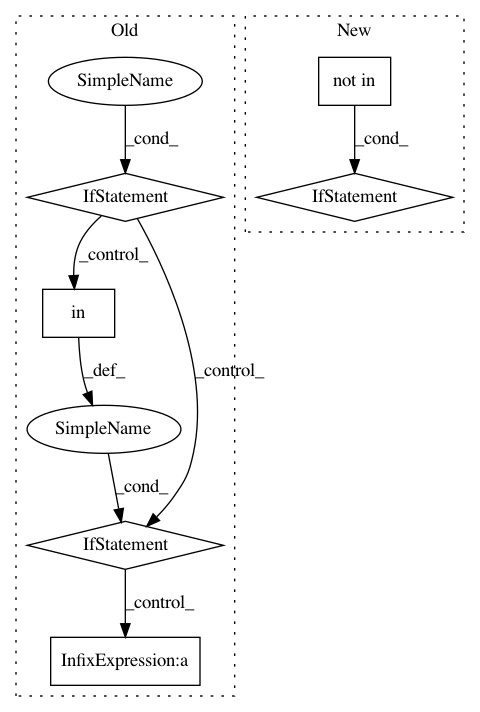
if self._has_no_bug(mutant):
for error in self.ERROR_STRINGS:
// Check if the error string is in the response
if error in response.body and \
error not in mutant.get_original_response_body():
desc = "A possible (detection is really hard...) format"\
" string vulnerability was found at: %s"
desc = desc % mutant.found_at()
v = Vuln.from_mutant("Format string vulnerability", desc,
severity.MEDIUM, response.id,
self.get_name(), mutant)
v.add_to_highlight(error)
self.kb_append_uniq(self, "format_string", v)
break
def _get_string_list(self):
:return: This method returns a list of format strings.
After Change
for error in self.ERROR_STRINGS:
// Check if the error string is in the response
if error not in response.body:
continue
if error in mutant.get_original_response_body():
continue
desc = ("A possible (detection is really hard...) format"In pattern: SUPERPATTERN
Frequency: 3
Non-data size: 6
Instances Project Name: andresriancho/w3af
Commit Name: c08c98415395b76371581432be55381f0f6e2b40
Time: 2018-01-09
Author: andres.riancho@gmail.com
File Name: w3af/plugins/audit/format_string.py
Class Name: format_string
Method Name: _analyze_result
Project Name: andresriancho/w3af
Commit Name: 5d0b89fa7644bdd51cb4615829cbd329898408a1
Time: 2019-06-07
Author: andres.riancho@gmail.com
File Name: w3af/plugins/audit/response_splitting.py
Class Name: response_splitting
Method Name: _header_was_injected
Project Name: ReactionMechanismGenerator/RMG-Py
Commit Name: c02df66939452dded7d83ac2bb422db76212eb8a
Time: 2020-04-26
Author: kspieker@mit.edu
File Name: rmgpy/tools/mergemodels.py
Class Name:
Method Name: combine_models